Creating Trust Online
No one can stop zero-day malware from entering your network, but
Comodo can prevent it from causing any damage.
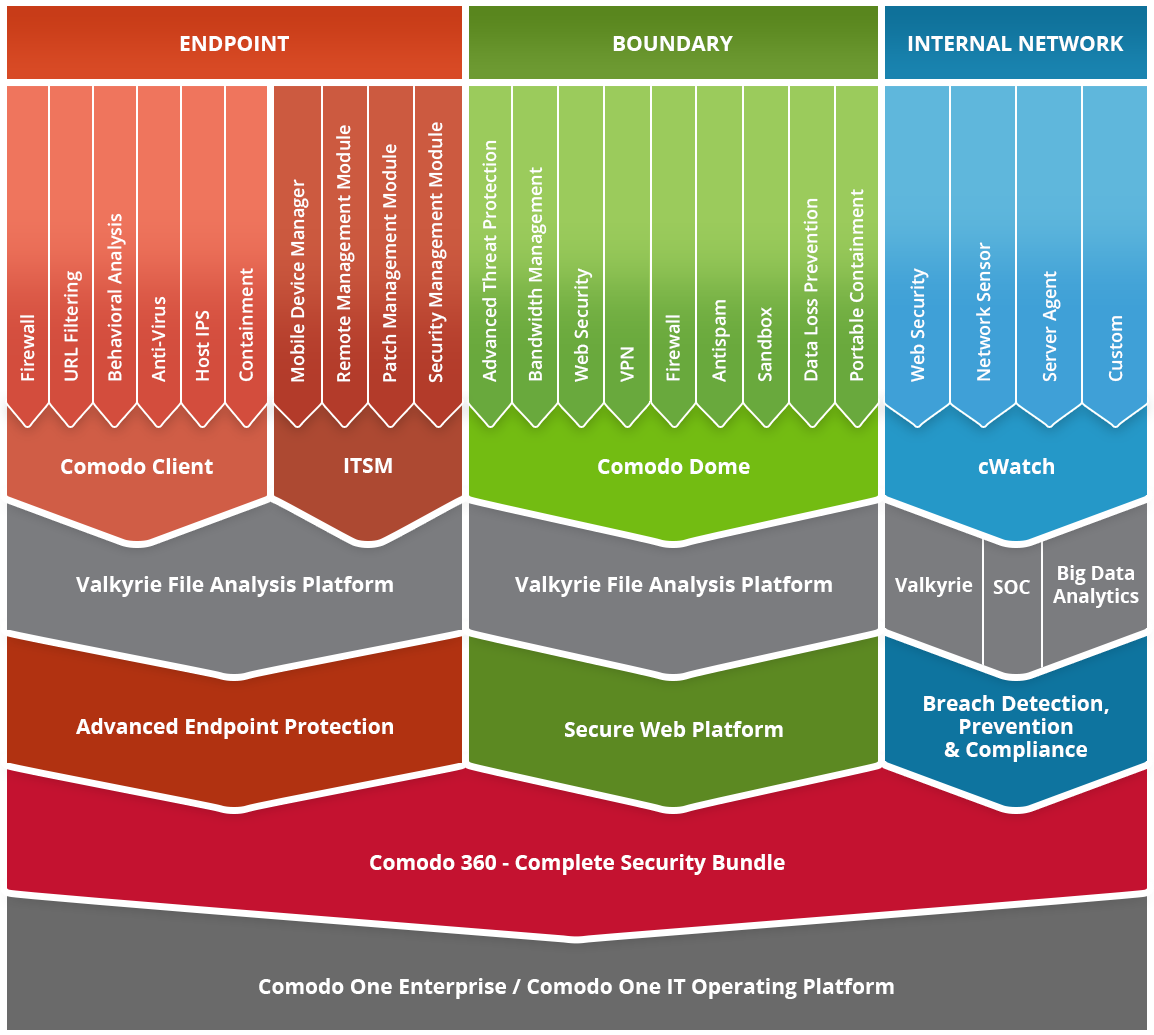
Comodo solves the most advanced malware problems with innovative solutions that secure the enterprise from both known and unknown threats across the endpoint, boundary and internal network.
of the Fortune 1000
business customers in 100 countries
business partners and affiliates
PC security installations
Why are data breaches on the rise? Enterprises keep getting infected because conventional endpoint protection solutions—including next-generation automated approaches—detect only the files and applications that are known to be bad. They allow everything else to run on the endpoint and this Default Allow posture is how zero-day threats get into your network.All hackers have to do is create new malware to avoid detection. Allowing only one percent of untrusted applications or processes to run in your enterprise invites attack.
Comodo is the only security vendor with a Default Deny platform that allows full usability of unknown files while they run in Secure Auto Containment™ until automatic and expert human analysis delivers a trust verdict of good or bad. Comodo Advanced Endpoint Protection is based on a Default Deny posture that allows the good applications, blocks the bad, and contains the unknown files pending analysis to prevent the damage from unknown malware. Only good files run unfettered on your endpoints.
Comodo’s Secure Auto Containment technology is extremely lightweight, has no CPU dependencies and is completely application agnostic. This gives enterprises and end users the best of both worlds: default deny security with default allow usability.
Comodo’s integrated solutions at the endpoint, boundary and internal network exchange threat intelligence and other information across the enterprise to prevent the damage from cyber-attacks. This helps enterprises lower costs while addressing their complete cybersecurity needs with greater operational efficiency.



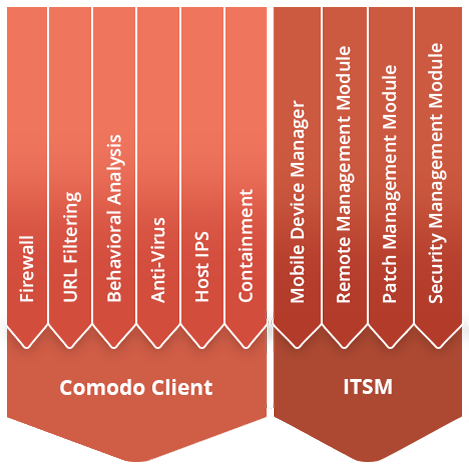
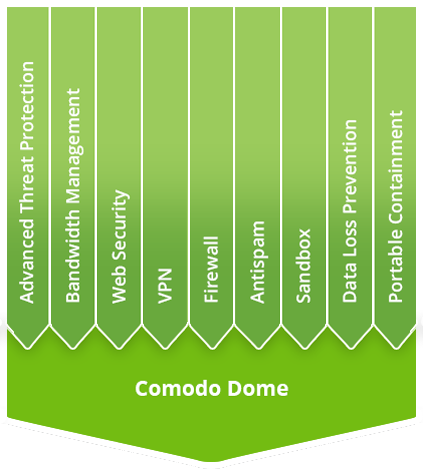
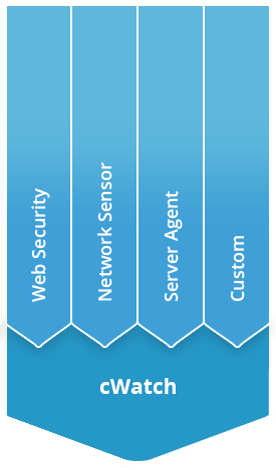


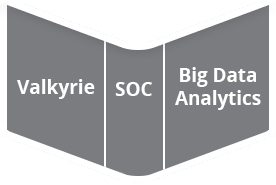





Please Contact Us
enterprisesales.india@comodo.com